Phishing/SPAM Example Series – Number 2
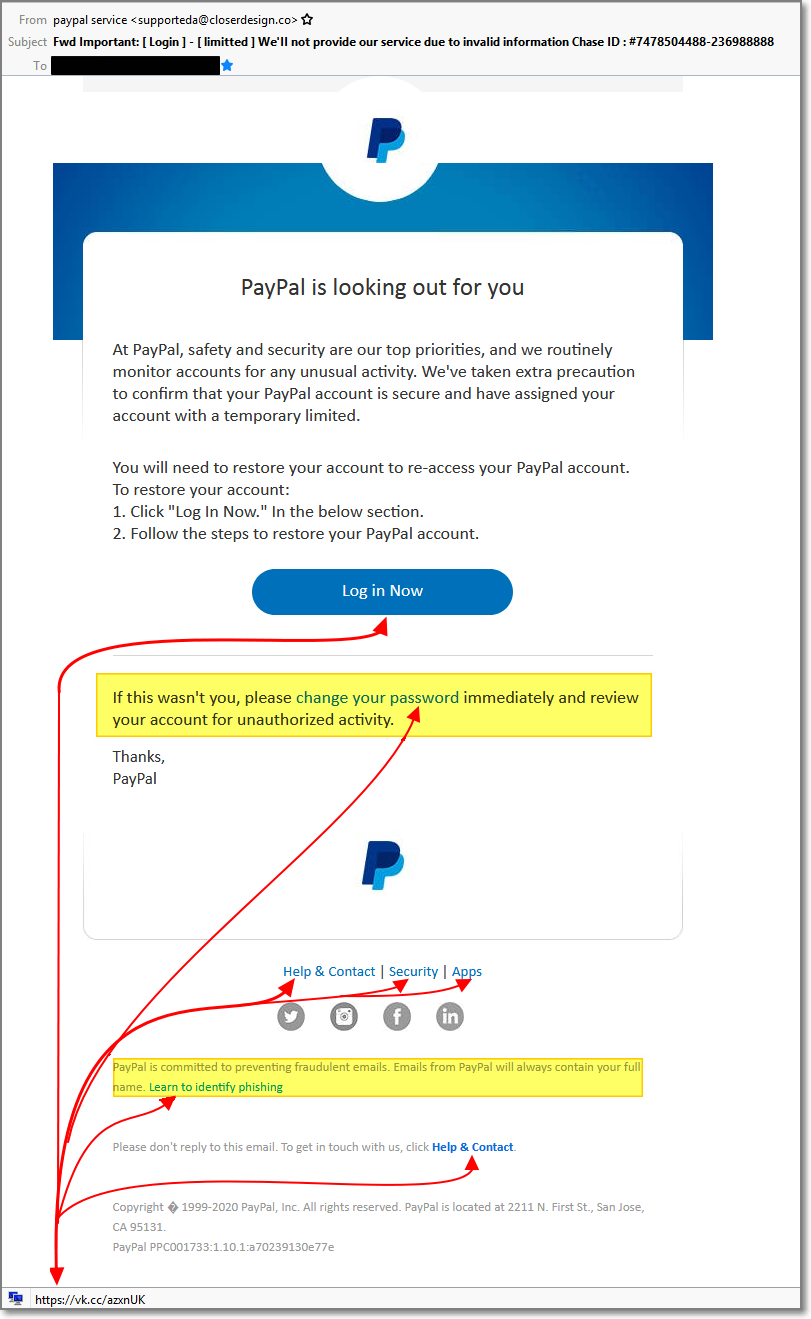
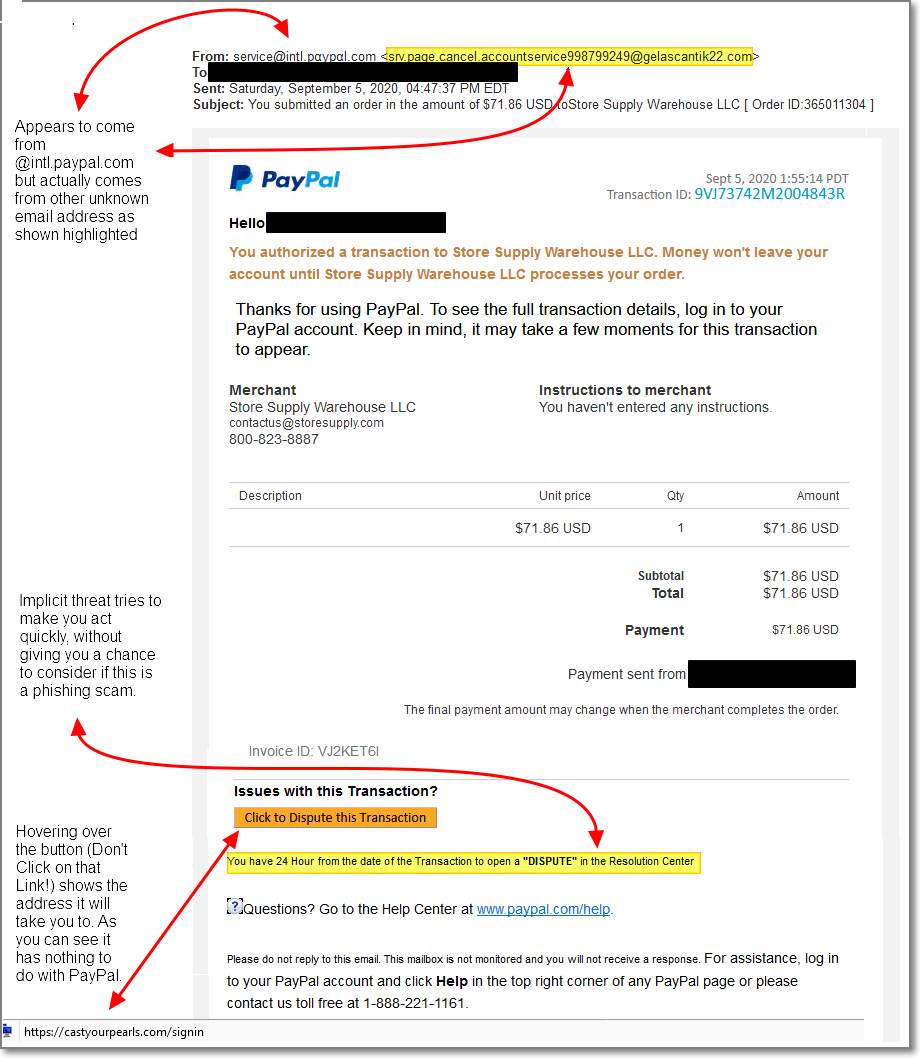
Photo by Brady Rogers on Unsplash Here is another “PayPal” email. This one purports to be “looking out” for me. All the links in the email (including the “change your password” and “Help & Contact” lead to https://vk.cc/azxnUK. Also note the actual email address (“closerdesign.co”), that has nothing to do with PayPal. Notice how they…