Be careful about clicking on links in emails that purport to be from your company helpdesk, CDC, Microsoft, your bank, the IRS, or another company that you deal with.
With this COVID19 running rampant, and more people working from home, your work IT support folks may not be readily available to answer your technical questions. Or, you may be a freelancer, self-employed, and you need to be your own IT support, solving your own problems. It’s in times like these when scammers easily find their victims. So one of the most important things you as a computer user can do, from a security perspective, is to safeguard your username and password to everything.
Many businesses (including the company I work for) have transitioned from using software applications locally installed on a computer to using web-based applications such as GSuite ( Google Docs, Sheets, Gmail, Hangouts) and Office365 (Excel, Word, PowerPoint, Outlook, and Teams). All of my calls with colleagues nowadays are through Microsoft Teams. Most of my chats are through Google Hangouts. And, as a remote user, web-based applications are easier to access from anywhere. As a developer you may be using Azure, AWS, or Google Cloud. HR and Payroll may be using something like ADP or Quickbooks.
With the prevalence of web-based apps, and more people working from home, along with the usual Facebook, Amazon, or Netflix type of personal accounts, more vectors are being introduced through which scammers can trick you into giving up your personal information. They are getting more ingenious and sophisticated. Take for example the following email:
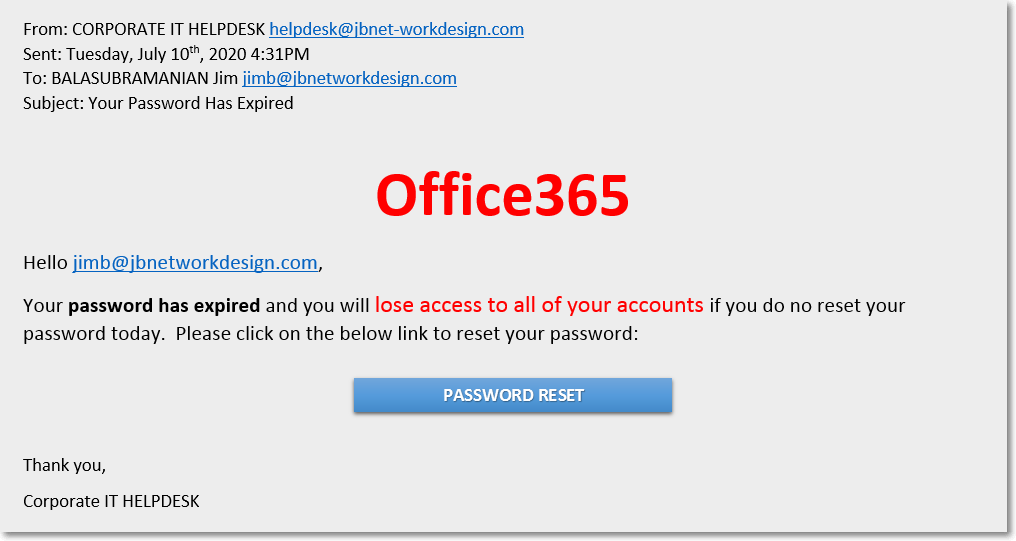
Office365 is telling me that my password expired and I have to reset it. For the untrained eye, it looks legit. I may be busy at the time I receive this email, working against the clock to meet a deadline for a project, and I can’t afford to be locked out of my account. I panic, and without thinking, I click on the Password Reset button. It takes me to a webpage where I can sign into Microsoft and reset my password:
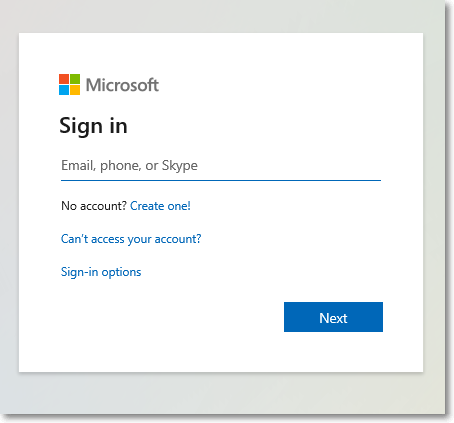
But what did I actually do? I just gave my username and password to some hacker. If you’re like most people (who don’t want to remember a billion different passwords), you may be using that username and password combination elsewhere, like to access your bank account (or worse, your Netflix account — we get to see what you’ve been binge watching while you’re “working from home”).
The email above is what is called a phishing email. Phishing emails can be crafted to look legitimate, with official company logos (pulled from public company webpages), important sounding headers like ”From: CORPORATE IT HELPDESK”, and big bold letters threatening a loss of account access. Clicking on the Password Reset button took me to a meticulously crafted, legitimate looking, sign-in page. All to give up my credentials to a hacker.
And the hacker doesn’t need 10, 100, or even 1,000 victims. To start, they just need 1 to fall for the scam. Once they have access to my email account, they can see what companies I deal with, maybe reset my banking password by using “Forget my password” link on the company sign-in page. They can see who my contacts are and send them emails pretending to be from me, the CIO, or ”From: CORPORATE IT HELPDESK”, and have my contact give up their personal information. In a large company, you’re bound to get users who unfortunately fall for the scam.
How to Spot a Phishing Email
Let’s take a look at the email above more closely:
- Look at the actual address the email is coming from.
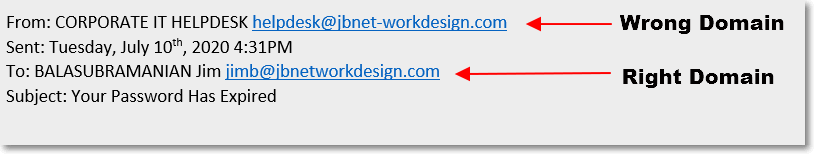
The domain the email is coming from looks like mine, jbnetworkdesign.com, but it has a dash in it. The email you receive may look like it’s coming from within your company, or from your bank (like bankoffamerica.com instead of bankofamerica.com), or even Microsoft (like microsft0365.com or ourlook.com). Look for subtle clues in the From: address section of the email that demonstrates that the email is not legit.
- Hover over (Don’t click!) the links or buttons to see the actual address they will take you to.
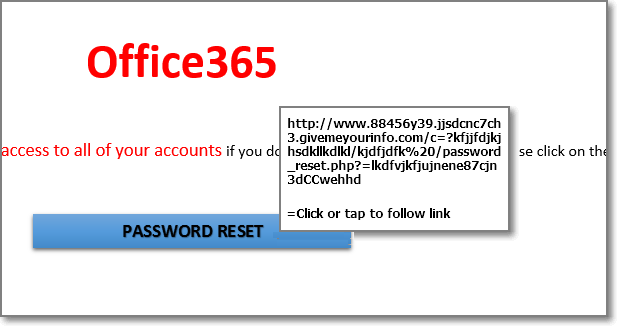
If you look at where the link or button will take you, it’s often some crazy long url (or a shortened url that’s trying to mask it’s true destination). In either case it would be something unrecognizable.
Here’s another example:
You may get an email claiming to be from Facebook support, saying you need to reset your password. In the email you see a link that says:
But if you hover over it, you can see it just brings you back to Medium (which in this case is a good thing!). But that’s how the scam works.
Other Types of Phishing
1. Confirm your Password or Update your Payment Method
With many people working from home, streaming services such as Netflix, Hulu, and Disney+ have seen a huge increase in subscribers. This also means it’s prime time for hackers who send out official looking phishing emails pretending to be from the streaming company and asking you to Confirm your Email, Update your Password, or Update your Payment Methods, getting you to inadvertently enter the information on a fake webpage that appears to be the actual streaming service page.
2. Emails with attachments
Password reset emails are not the only type of phishing emails out there. Our finance folks often receive emails with scary subjects like FINAL NOTICE, INVOICE ATTACHED, or PLEASE PAY UPON RECEIPT, with what appear to be a PDF attachment in the body of the email, but instead it would actually be an image of a PDF document icon. They would, by habit, double-click to try to open the attachment but instead of opening a document they would be clicking on a link, that would launch their browser and open a fake webpage, where again they would be asked to enter their credentials.
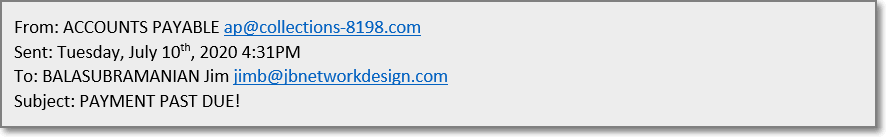

I’ve also seen Human Resources receive emails, from “background check” companies looking for information on employees. Or attachments that look like resumes from people looking for work.
3. Beneficiary: a million dollars waiting for you!
This is to re-inform you that you have been shortlisted among the few lucky people to receive Five Hundred Thousand United States Dollars Non-Profitable charity funds from our deceased parents in your Name.
Your email was selected using a Random Email Picker Tools used today 7/11/2020 7:19:30 p.m..
Kindly get back to me on how your fund can get to you.
God Bless you
Kind Regards
Mrs. Louise Gill.
I probably get an email like this every day. It passes through any spam checker because there is nothing technically odd about the email. No attachments, no links. The hacker just wants you to reply back to start the conversation to get you to give up your info. It’s a bit of what’s called social engineering. And if you don’t know any better, down on your luck, need cash, especially in these trying times, you may do it.
Don’t.
But it’s easy to fall prey to social engineering. Just ask Twitter! Some Twitter employees apparently fell for it and gave up access to internal tools. As a result, some high profile Twitter accounts (President Obama, Elon Musk, Kim Kardashian, among others) were used to tweet out a Bitcoin scam.
4. Hey it’s <insert name of your CEO here>. I’m stuck at the airport and my credit card is not working. Can you wire me $5,000?
Trust me, emails like this get through spam filters. And sometimes, an employee falls for it. Educate your employees.
5. Hi grandma it’s your grandson!
Another bit of social engineering, preying on our senior citizens. My mom got a call once from someone pretending to be my son in trouble. First off, my son doesn’t call my mom grandma. With my mom being from South India, he calls her Paatti. So she knew something was phishy (get it?) and called me to make sure my son was ok. My parents also get the calls from the “IRS”, “FBI”, “Microsoft Tech Support”, “Police Charity”, and the “Social Security Administration”. They don’t fall for it. I taught them well.
If you have parents or elderly neighbors that you take care of or keep an eye on, please make sure they are aware of these cold call scams.
6. Your COVID-19 Economic Stimulus Relief Payment is waiting (or Your PPP Loan has been APPROVED)
Unfortunately, scammers come out in full force when we’re at our most vulnerable. Phishing emails are being sent at an alarming rate from senders pretending to be from the CDC, Federal or State governments, or local hospitals. With the fake COVID-19 emails, scammers can get you to give up even more personal information like your Social Security number or Bank Routing and Account numbers.
What You Can Do to Not Become a Victim
First and foremost, be wary of the emails you receive. Ask basic questions like:
- Was I expecting this email?
- Is the email coming from a real address that I’ve seen before? (don’t just look at the name, look at the actual address)
- Do I know the sender?
- Am I expecting this attachment?
Don’t immediately click on links or attachments. Hover over them and make sure they are going to addresses and domains you recognize.
No company is going to send you an unsolicited email to reset your password or request your login info.
Not Microsoft, not Facebook, not Amazon, not Netflix, not your bank. NO ONE. Unless they themselves have been hacked and your information has been compromised, in which case they should go public about the hack, they should have reset your password already, you would have heard about it in the news, and you would be expecting the email.
But even so, if you think your password has expired or has been compromised, open up a web browser, go directly to the website of the company in question by typing in their address or using your bookmarks, and login/reset there. Don’t click on the links in emails.
If available, use Two Factor Authentication or Multi-Factor Authentication.
Some online web-based applications offer 2FA/MFA as a second level of security. Typically it involves, in addition to using your username and password, getting a code on your phone or using some sort of Authenticator Application, like Google Authenticator, and entering that code on the website. The idea is, even if your password is stolen, only you would have access to your phone, so the hacker still won’t be able to get through without it. Most large companies use 2FA/MFA to provide access to company resources from outside the company network and that’s great! But that same username and password combination might be used for other outside apps that you access where you don’t have 2FA/MFA enabled. So that leads to the next tip.
Use different passwords for different applications.
You may have to use the same username (many companies use the email address as a username). But don’t reuse the same password for everything even if it is easier to remember. And try to make it complex. At least 8 characters, uppercase, lowercase, numbers, special characters. And change your passwords often, like every few months.
Look, these are tough times and these precautions are a PITA. But scammers are opportunists that are out there trying to get you to give up the keys to the house. And once they get access, they can do serious damage. So be on alert, look out for the phishing emails, and don’t fall for the social engineering tactics. Computer security really is a 24x7x365 job. When in doubt, ask someone. AND DON’T CLICK ON THE LINKS!
This post originally appeared on Medium – On how to avoid becoming a phishing victim.
